On my Windows 10, notebook (and several other PCs), I found several errors like the following one during the system startup:
Event 10016, DistributedCOM
The application-specific permission settings do not grant Local Activation permission for the COM Server application with CLSID
{D63B10C5-BB46-4990-A94F-E40B9D520160}
and APPID
{9CA88EE3-ACB7-47C8-AFC4-AB702511C276}
to the user NT AUTHORITY\SYSTEM SID (S-1-5-18) from address LocalHost (Using LRPC) running in the application container Unavailable SID (Unavailable). This security permission can be modified using the Component Services administrative tool.
As reported in the event description, the solution seems really simple. You only have to use the ‘Component Service Administrative Tools’, to fix the problem.
Here you probably face some unexpected troubles:
- first is to find out which is the reported application.
- second is that application property pages are almost fully disabled.
After some investigations, I found out how to overcome and fix the problem.
My Solution
In the event description we have to care about the following 3 items:
The application-specific permission settings do not grant Local Activation permission for the COM Server application with CLSID
<UUID1>
and APPID
<UUID2>
to the user <USER_ACCOUNT> SID (S-1-5-18) from address LocalHost (Using LRPC) running in the application container Unavailable SID (Unavailable). This security permission can be modified using the Component Services administrative tool.
- open ‘regedit.exe’ with administrative access rights.
- from the Event Viewer, copy the <UUID1> (ie the first bold hex string) in the clipboard.
- switch to Registry Editor, select Computer node (the root one), press Ctrl+F, and paste <UUID1>.
- when the research ends at a node (in the treeview on the left), right-click it, click on ‘Permissions’, and click on ‘Advanced’ button.
- change ownership to ‘administrators’ to this object and all its descendants.
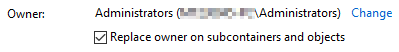
- if needed, add ‘administrators’ to the permission entries in order to have ‘Full control’ access rights, and apply this to all its descendants.
- keep a note of (default) value.
- apply the same procedure to the second <UUID2>.
- open ‘dcomcnfg.exe’
- select ‘Component Services/Computers/My Computer/DCOM Config’ and locate the related Server application by its name (from our previous note), or by its AppID (the <UUID2>).
- right-click the entry, select ‘Properties’, and go to ‘Security’ tab.
- under ‘Launch and Activation Permissions’, click on ‘Customize’ and then press ‘Edit’ button.
- add <USER_ACCOUNT> in order to grant ‘Local Launch’ and ‘Local Activation’ access rights.
- click on ‘OK’ buttons and close the application.
Notes
The sequence I found is to fix any reported Event 10016 object, by applying the above procedure.
Then reboot, and look for any new Event 10016.
The second note is that we can restore the original owner and access rights to the updated UUIDs, but the cure may be worse than the disease. The procedure to do this is long, tricky, and boring, i.e. we can easily do errors that wipe out our intervention benefits. Up to now, I leave the updated access rights since the previous owner (usually the Trusted Installer) wasn’t able to set up the DCOM application properly.